Microsoft Identity Platform
The Basics
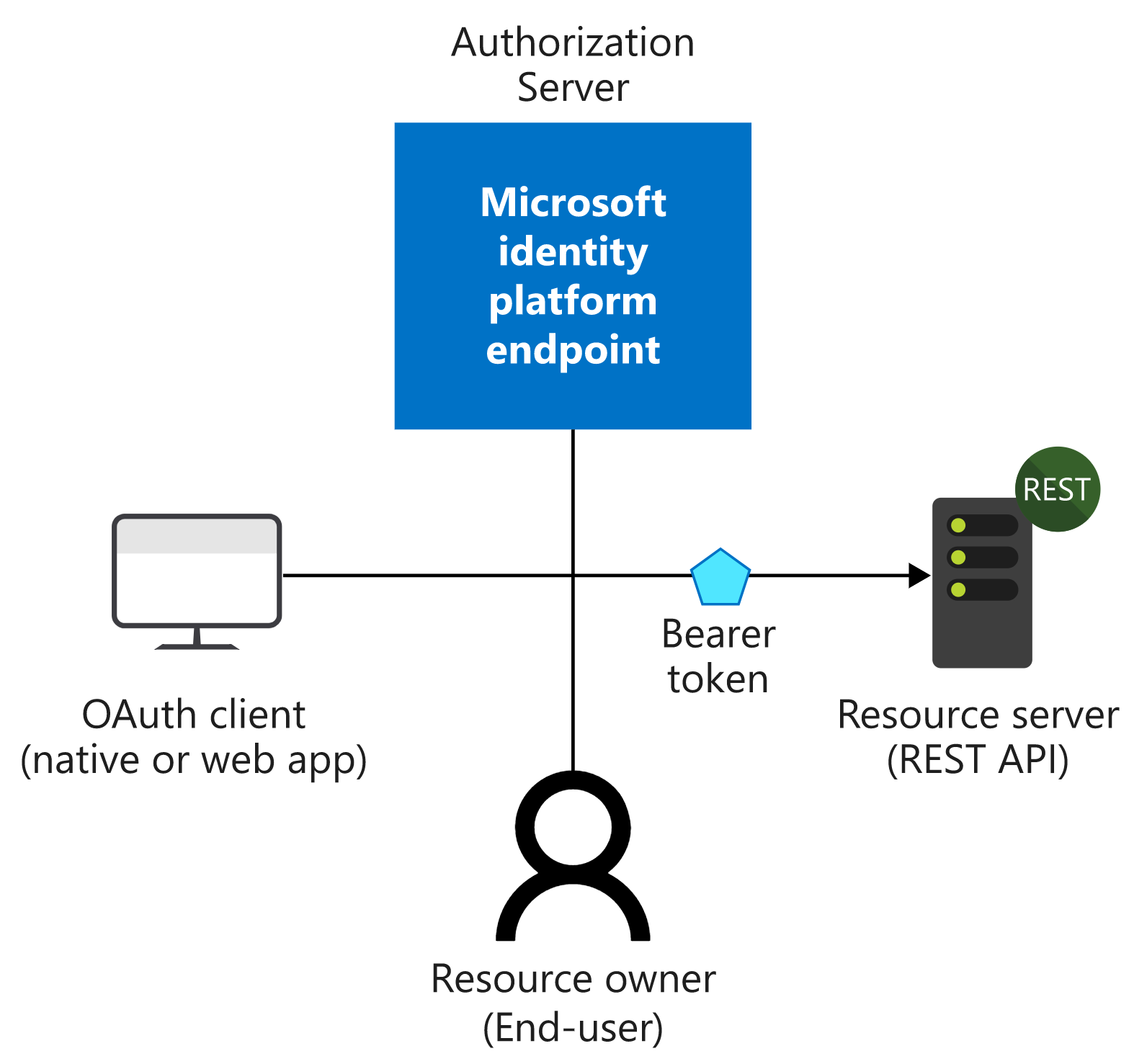
- The Authorization Server is the Microsoft identity platform and is responsible for ensuring the user’s identity, granting and revoking access to resources, and issuing tokens. The authorization server is also known as the identity provider - it securely handles anything to do with the user’s information, their access, and the trust relationships between parties in a flow.
- The Resource Owner is typically the end user. It’s the party that owns the data and has the power to allow clients to access that data or resource.
- The OAuth Client is your app, identified by its application ID. The OAuth client is usually the party that the end user interacts with, and it requests tokens from the authorization server. The client must be granted permission to access the resource by the resource owner.
- The Resource Server is where the resource or data resides. It trusts the Authorization Server to securely authenticate and authorize the OAuth Client, and uses Bearer access tokens to ensure that access to a resource can be granted.
App Registration
- An Application ID that uniquely identifies your app
- A Redirect URI (optional) that can be used to direct responses back to your app
- A few other scenario-specific values.
Endpoints
Once registered, the app communicates with the Microsoft identity platform by sending requests to the endpoint:
1 | https://login.microsoftonline.com/{tenant}/oauth2/v2.0/authorize |
Tokens
// TOASK: How can bearer token ensure security in HTTP request? Can eavesdroppers get the header token?
- Access tokens - tokens that a resource server receives from a client, containing permissions the client has been granted.
- ID tokens - tokens that a client receives from the authorization server, used to sign in a user and get basic information about them.
- Refresh tokens - used by a client to get new access and ID tokens over time. These are opaque strings, and are only understandable by the authorization server.
Authorization Grant Types
Authorization Code Grant Flow
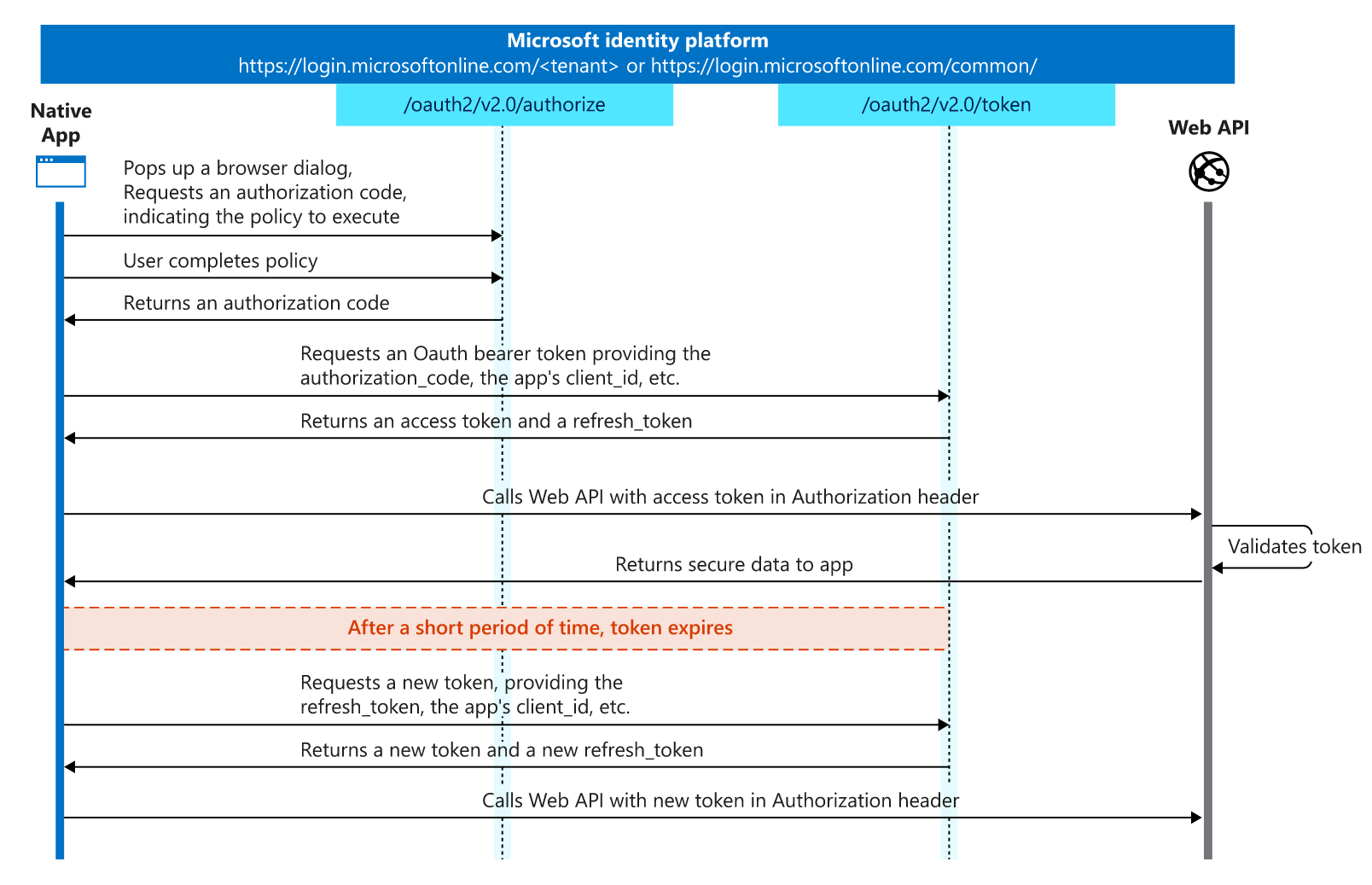
// TOASK: How does Web API validate token??
Request an authorization code.
1
2
3
4
5
6
7
8
9
10
11// Line breaks for legibility only
https://login.microsoftonline.com/{tenant}/oauth2/v2.0/authorize?
client_id=6731de76-14a6-49ae-97bc-6eba6914391e
&response_type=code
&redirect_uri=http%3A%2F%2Flocalhost%2Fmyapp%2F
&response_mode=query
&scope=https%3A%2F%2Fgraph.microsoft.com%2Fmail.read%20api%3A%2F%2F
&state=12345
&code_challenge=YTFjNjI1OWYzMzA3MTI4ZDY2Njg5M2RkNmVjNDE5YmEyZGRhOGYyM2IzNjdmZWFhMTQ1ODg3NDcxY2Nl
&code_challenge_method=S256Request an access token
1
2
3
4
5
6
7
8
9
10
11
12
13// Line breaks for legibility only
POST /{tenant}/oauth2/v2.0/token
Host: https://login.microsoftonline.com
Content-Type: application/x-www-form-urlencoded
client_id=6731de76-14a6-49ae-97bc-6eba6914391e
&scope=https%3A%2F%2Fgraph.microsoft.com%2Fmail.read
&code=OAAABAAAAiL9Kn2Z27UubvWFPbm0gLWQJVzCTE9UkP3pSx1aXxUjq3n8b2JRLk4OxVXr...
&redirect_uri=http%3A%2F%2Flocalhost%2Fmyapp%2F
&grant_type=authorization_code
&code_verifier=ThisIsntRandomButItNeedsToBe43CharactersLong
&client_secret=JqQX2PNo9bpM0uEihUPzyrh // NOTE: Only required for web apps. This secret needs to be URL-Encoded.Refresh the access token
1
2
3
4
5
6
7
8
9
10
11// Line breaks for legibility only
POST /{tenant}/oauth2/v2.0/token
Host: https://login.microsoftonline.com
Content-Type: application/x-www-form-urlencoded
client_id=6731de76-14a6-49ae-97bc-6eba6914391e
&scope=https%3A%2F%2Fgraph.microsoft.com%2Fmail.read
&refresh_token=OAAABAAAAiL9Kn2Z27UubvWFPbm0gLWQJVzCTE9UkP3pSx1aXxUjq...
&grant_type=refresh_token
&client_secret=JqQX2PNo9bpM0uEihUPzyrh // NOTE: Only required for web apps. This secret needs to be URL-Encoded
Authorization Code Flow (with PKCE) for SPA
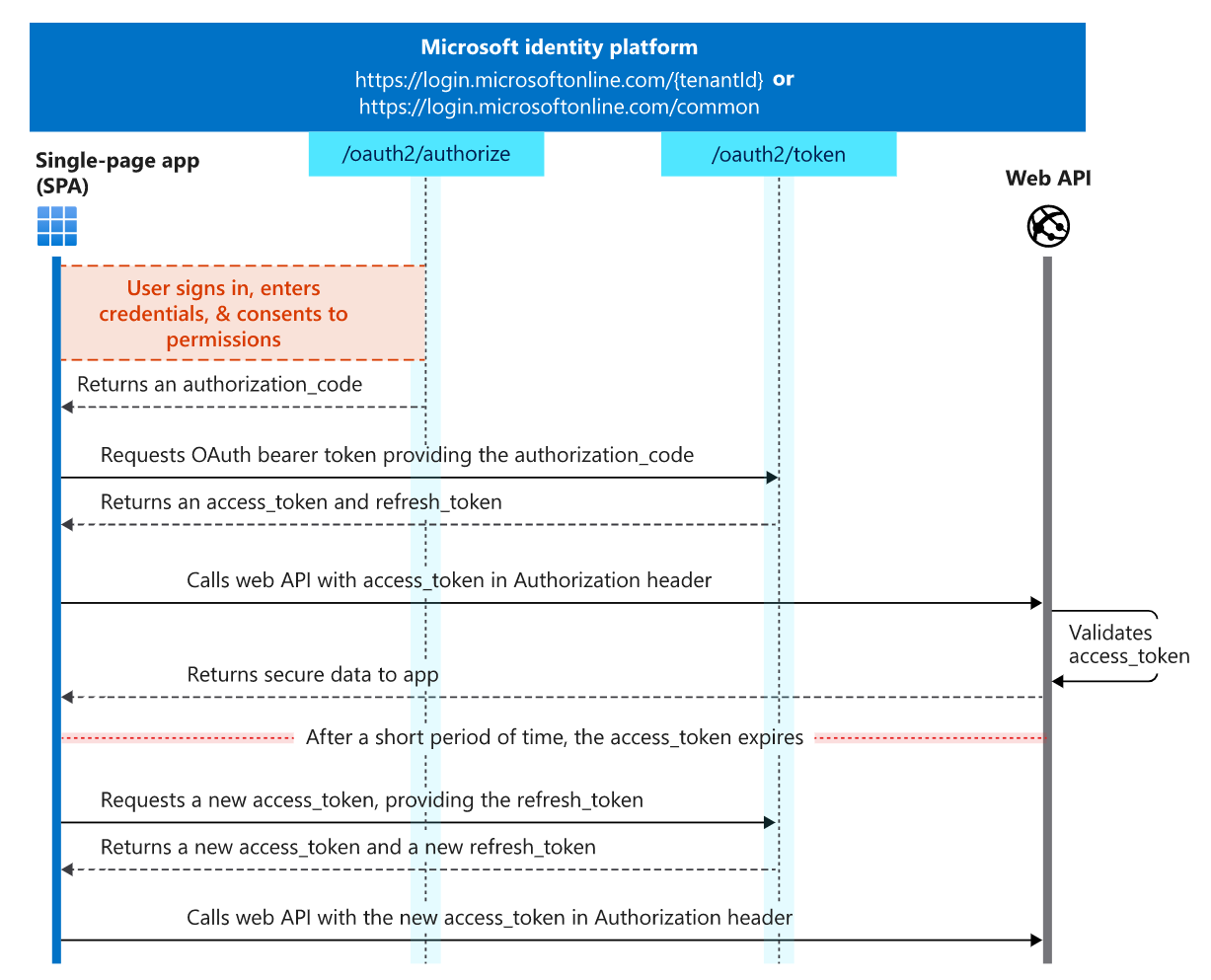
// TOASK: Is it secure to use auth code in SPA when using PKCE?
Implicit Grant Flow
- Note: With the plans for third party cookies to be removed from browsers, the implicit grant flow is no longer a suitable authentication method. authorization code flow is recommended for all new applications including SPAs.
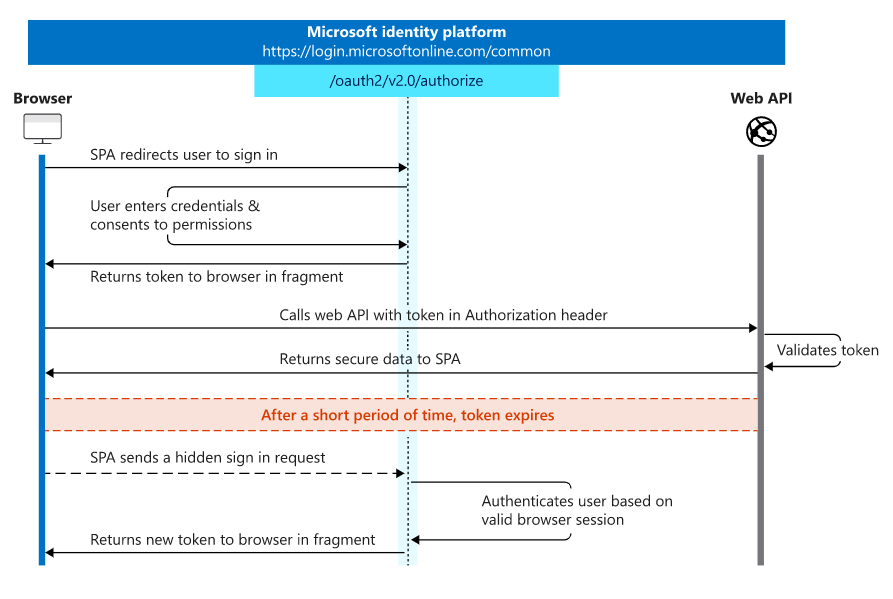
Resource Owner Password Credentials
Client Credentials
Example
In our implementation, Tab app uses authorization code flow with PKCE.
- Tab App frontend gets auth code.
- Frontend browser pop up login page (/public/auth-start.html).
- User login and consent, frontend page redirect user to redirect_uri (/public/auth-end.html).
- End page parse authorization code and return to tab app.
- Tab App sends the auth code to backend auth server to get access token.